Jon Hayter describes how organisations can innovate their security strategy to become fit-for-purpose in an interconnected, and more dangerous, global business environment.
We are in a time of unprecedented threat and it is only through an innovative and forward-thinking approach to confronting these threats that we can hope to keep our businesses, buildings and, most importantly, people safe.
The current threat level to Britain is assessed as severe, meaning that an attack is highly likely. The level of threat is complex and ranges from individuals carrying out stand-alone attacks to sophisticated networks executing innovative and audacious plots.
We have all watched in horror at the recent atrocities which have unfolded before our eyes with devastating impact. Each new incident brings with it a unique set of questions, learning points and a familiar sense of fear that we or someone we know will be the next victim.
I feel and understand that fear, and having served in the police force for over 30 years, I realise that the ability to properly understand our challenges is crucial to maximising success.
Beyond the ambit of terrorism, organised criminal gangs are continuing to build robust operations networks and are mobilising their resources with alarming efficiency.
The risk posed by insider threats is stark and wide reaching. Whether it’s a disaffected member of staff or an employee associating with known criminals, the danger is real, and the economic implications are grave.
Now, more than ever, it is essential that we do everything we can to help protect the security of our critical national infrastructure, businesses and public places. There is no room for complacency, no second chance to get it right.
Lessons from the Battlefield
The police, security and intelligence services are working tirelessly and at pace to confront terrorism and organised crime, but in the face of searing budget cuts and competing demands, they alone cannot guarantee safety.
It has been said that “Those who fail to learn from history are doomed to repeat it”, and it is that philosophy that underpins our ability to meet new and emerging threats.
A few years ago, while on holiday, I encountered a retired colonel from the US Rangers. The colonel, whom I feel privileged to call a friend, told me about his experience of serving in the Vietnam War.
He paid homage to his forefathers and explained how it was the knowledge they passed down to him that helped bring about success on the battlefield. He understood that by adopting the mindset of the enemy and predicting their likely future behaviour, you can put together a much more complete picture of your environment and deploy your resources more effectively.
His approach resonated with my experience of planning and command where ‘getting into the head of a hostile’ is essential to mitigate risk. Malcolm Gladwell describes this concept as “thin slicing” – the utilisation of small slivers of information about a person with the objective of forming a wider opinion about their character and intentions.
A Strategy Equipped to Meet New and Emerging Threats
Earlier this year, former UK Security Minister, Admiral Lord West of Spithead pronounced “Terrorists are good at learning from each other, we should be too…. The tempo and ferocity of recent terrorist attacks are now the new norm and not a blip”.
Further attacks are inevitable and forward-thinking organisations understand the importance of continually reviewing and adapting their strategy to stay ahead of the curve. While there is no magic bullet that can stop crime before it happens, there are many steps you can take to enhance your strengths and significantly improve your capacity.
Gone are the days when traditional security arrangements such as CCTV and intruder alarms were enough to protect your organisation from emerging threats. Lessons learnt from recent incidents point to an increasingly interconnected world – a technologically advanced world where data crunching algorithms, online footprints and deterrence messaging are just as important to security infrastructures as traditional security measures.
At the same time, rapid developments in technology and communications enable hostiles to gather and verify information quickly, easily, and at the touch of a button. Information gathering is a vital component of the attack planning process; it is essential to not only plan an attack with the confidence of success but assess the likelihood of succeeding.
According to academic research, information gathered is used by hostiles in three main ways to:
- Assess the state of security and the likelihood of detection during reconnaissance
- Identify vulnerabilities in security and establish how these could be exploited to achieve the desired outcome
- Inform the modus operandi of criminal activity and assess the likelihood of success without obtaining meaningful information during hostile reconnaissance, it is difficult to carry out a successful attack. Whether it’s securing a major stadium event or protecting your assets, a communications strategy that takes account of technological advancements and changing trends is necessary to ensure you meet the challenges of emerging threats.
Don’t Get Left Behind
All good businesses know if you stand still you are in danger of getting left behind. As the nature of the threat has evolved, so too has our methodology and approach. By walking in the shoes of those who threaten our interests and replicating their attack planning process, we are constantly adapting to meet the changing threat picture.
The application of this approach will enable us to determine:
- What information about your company, its staff and its assets are available online and determine how this information will help hostile(s) target you
- The security culture of your staff and organisation in general. This will enable the audit of staff culture and form the start point of any required action for senior management to direct informed changes
- The vulnerability of staff to social engineering by the hostile penetration of social media and other open sources of information
- The vulnerability of staff when travelling to and arriving at a set destination
- How to target-harden your workplace, home address or venues to be visited by you or your staff to prevent acts of hostility
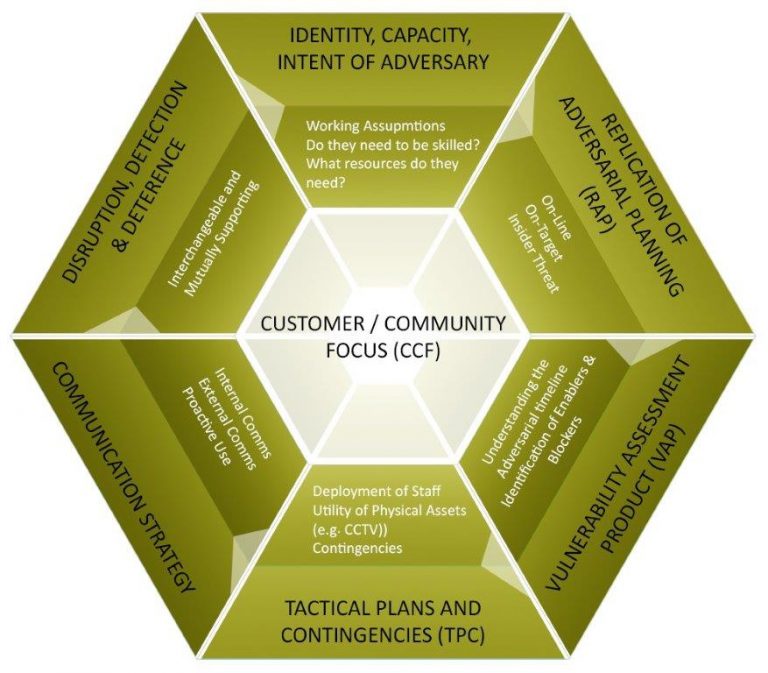
This Process is Known as the Adversarial Planning Model (APM)
The APM delivers a flexible approach built to prevent the variety of threats we face, from terrorism and criminal action through to corporate-sponsored espionage, delivering a range of solutions focusing on the following key areas.
- Denying others the ability to obtain the information they require for success
- Review and improvement of organisational processes and procedures
- Review and adjustment of communication strategies, both internal and external
In our world of risks and competing demands, don’t work harder; work smarter.
The need to have the ability to reinvent ourselves, from individual skills to strategic policies and planning will become essential to success because our adversaries will reinvent themselves and they are not necessarily restricted by laws and morals in the same way that we are.
Want to make sure you have a solid security strategy in your organisation? Check out Cardinus’ latest security services, provided by our experts in personal and corporate security.